Quantum complementarity, or the inability to measure multiple observables simultaneously, is a unique and fundamental feature of quantum mechanics. The feature’s indispensability is now reinforced in cryptography --- the new results jointly completed by researchers from Prof. Xiongfeng Ma’s research group at the Institute of Interdisciplinary Information Sciences (IIIS) and the University of Toronto exhibit how it leads to perfect privacy even without trusted devices, an impossible task in a classical world. The research results were recently published in the journal Physical Review Letters.
Quantum physics promises complementary observables like position and momentum, where the full knowledge of one property implies the ignorance of the other. In the quest to understand quantum physics, complementarity is closely related to entanglement --- a nonlocal physical state between distant parties that Einstein termed “a spooky action.” However, the concepts become much subtler in the device-independent regime that offers security without device characterization. Security proofs of device-independent quantum cryptography tasks are often complex and quite different from those of their more standard device-dependent cousins. The existing proofs pose huge challenges to experiments, among which large data-size requirement is a crux.
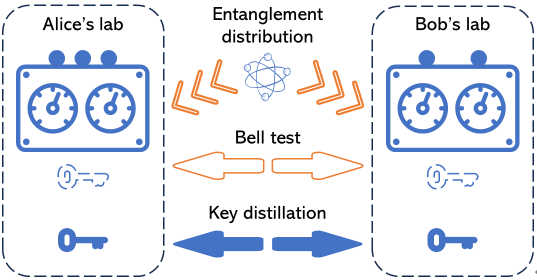
Figure 1. An illustration of the device-independent cryptography
In the new work, researchers explicitly show the complementarity security origin of the device-independent tasks. In a conceptually simple picture of quantum error correction, information leakage in a device-independent scheme is reflected from errors in quantum measurements, and complementary observables contribute to proper error-correcting codes. In addition, via generalizing the concept of sample entropy in classical Shannon theory and combining the martingale theory, the researchers developed a new parameter estimation method that applies to general non-independent-and-identically-distributed statistics, guaranteeing a complete security analysis that remains valid under the most general attack.

Figure 2. An illustration of security analysis process
With a better understanding of complementarity, the new analysis easily combines device-independent cryptography with data post-processing techniques such as advantage key distillation. Moreover, with the new analysis applied to the first experimental demonstration of device-independent quantum key distribution, the experimental time can be reduced to a third or even less of that required by previous state-of-the-art methods, bringing applications of device-independent cryptography to a more practical regime.

Figure 3. Comparison of analysis methods
The first author of this work is Dr. Xingjian Zhang, a 2023 Ph.D. alumnus of IIIS. The corresponding authors include Prof. Hoi-Kwong Lo at the University of Toronto and Prof. Xiongfeng Ma. Other authors include Dr. Pei Zeng, a 2020 Ph.D. alumnus of IIIS, and Tian Ye, a 2021 undergraduate alumnus of IIIS (Yao Class). The work was supported by the National Science Foundation of China.
Paper link: https://link.aps.org/doi/10.1103/PhysRevLett.131.140801
Editor: Li Han

